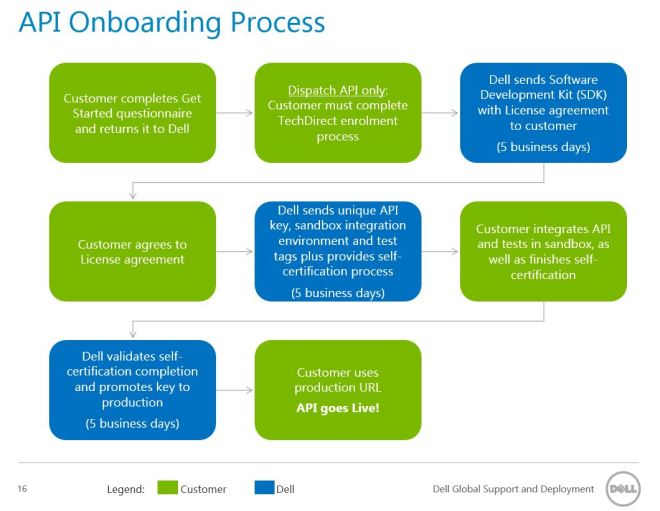
This blog will be the first part of a series about my Asset Management solution for SCSM 2012 R2. It will give a general overview about the solution. The following parts will go into the details.
Part 2: Authoring – Classes and Relationships
Part 3: Authoring – Folders and Views
Part 4: Authoring – Forms
Part 5: Reports
Part 6: Runbook/Automation details
I was asked by a colleague end of last year, if we can manage hardware assets with System Center Service Manager 2012 R2. I found a solution from Steve Beaumont for SCSM 2010 besides the solutions with costs from Cireson or Provance for example. I contacted Steve and after discussing the options I started to create a new solution for SCSM 2012 R2 based on Steves template. The new solution is designed to meet the requirements of the requesting company but can also be adopted to other companies needs.
The solution covers the following requirements:
- Sync with Active Directory (User), SCCM (PCs)
- Assets should stay in the DB
- Custodian should be linked to Asset
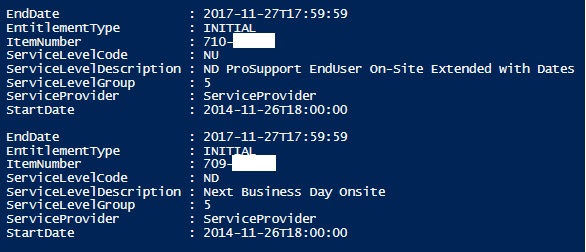
- Read PC warranty information from Dell
- Fill location information automatically
- Additional categories for Computer Assets: Kiosk, Lab, Test
- Create Assets automatically based on existing Windows Computer objects in SCSM (sync with SCCM)
- Email notifications for new/deleted/updated objects
Prerequisites:
- The Windows Computer names need to follow this structure: ❤ letter site Code><Serialnumber>.
- Enable AD and SCCM connectors in SCSM.
- Install Service Management console and SMlets on the Orchestrator Runbook Server.
How is this implemented?
To achieve that the asset stays in the DB, the solution creates an Asset class based on the ComputerHardware class. When a new Asset gets created then it needs to be assigned to the Windows Computer object. The Orchestrator automation runbooks are handling that. So it can happen that multiple Windows Computer objects which are created in SCSM get linked to one Asset object. With that you can see the history of the Asset deployment.
The Custodian also needs to be linked to the Asset, because the Asset is the hardware that should have a defined owner, which does not change when the system gets reimaged. The automation will take the primary user of the deployed Windows Computer as first Custodian, but this needs to be manually reviewed, because this could not be the real owner of the hardware (shared machines, etc.).
Classes and Relationships:

An Asset Management workspace is created and views for the new classes and some additional useful views.

This form shows which information can be entered for the ComputerAsset. The other asset forms look nearly the same (only the Category field is missing).
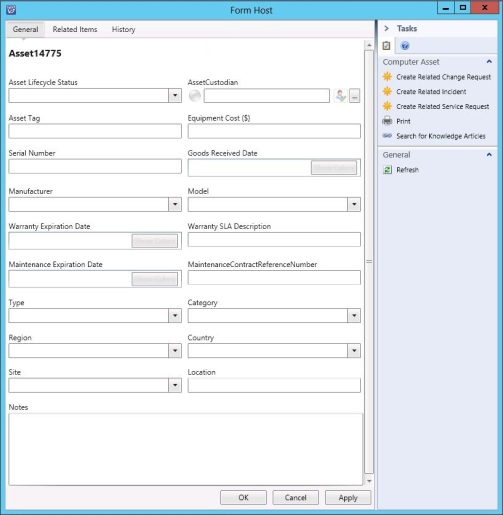
The Custodian can be selected in the AssetCustodian field. All other drop down fields reference predefined liss. The Windows Computer can be assigned in the Related Items tab. Also the Order can be referenced there.
The order form is very short and simple.
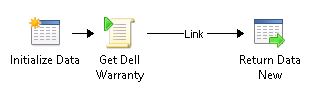
Some runbooks are created in Orchestrator to automate the creation of the ComputerAsset objects in SCSM and keep them updated, . Here is a short overview:

All three main runbooks (Create Asset, Update Asset, Check deleted Windows Computer) check the Windows Computer objects first, then the Computer (Deployed) objects (synced from SCCM) and at last checks if an Asset object exists.
Additionally to that sub workflows are called to check the location, get the warranty, etc.
General considerations
- Not everything can be automated, so every created/updated/deleted asset needs to be reviewed. Emails are send out to inform responsible teams to review.
- The solution is an example how hardware asset management can be done with SCSM. It can be extended with additional class types, other properties, different automation, etc.
The solution can be downloaded from Github and you can watch a video on YouTube, which shows the solution in the SCSM console and the Orchestrator runbooks. I already presented about this solution at a German conference. So if you want to watch a German video, then you find it here.
In the other parts of my series I will go into more details how the solution is designed. So stay tuned ;-).